If you’ve recently built a data security and risk management program and passed a security audit, you’ve accomplished more than many organizations. But cyber criminals don’t rest, even if you have a verifiable cybersecurity plan in place, bad actors are constantly innovating and finding new ways to infiltrate your systems. Many of the brand name companies who have suffered major breaches have completed security audits. For example, in 2015 Anthem suffered a significant breach even after passing a HITRUST audit, explaining the breach fell outside the scope of the audit. We also wrote a blog post about Zoom who has received their fair share of criticism directed at their security program despite promoting their SOC 2 compliance.
So it is essential not to look at security as a destination, rather a constantly evolving journey. Not only does your organization regularly change and evolve, but the requirements of your customers change too. And as we mentioned, bad actors are always looking for ways to reinvent themselves.
Could you do more to improve your cybersecurity program?
The resounding answer is Yes! There is always room for improvement and by using a platform, like Ostendio MyVCM, that grows with your company, you will be able to use work you have already completed to expand your solid start. Evidence and documentation that you gathered when building your framework data security program and preparing for your initial security audit can be used again when you broaden your goals.
By using a platform that has built-in questionnaires relating to well-known standards such as SOC 2, HITRUST, NIST 800-171, ISO 27001 and FedRAMP, building out the scope of your data security program is easier than you might think.
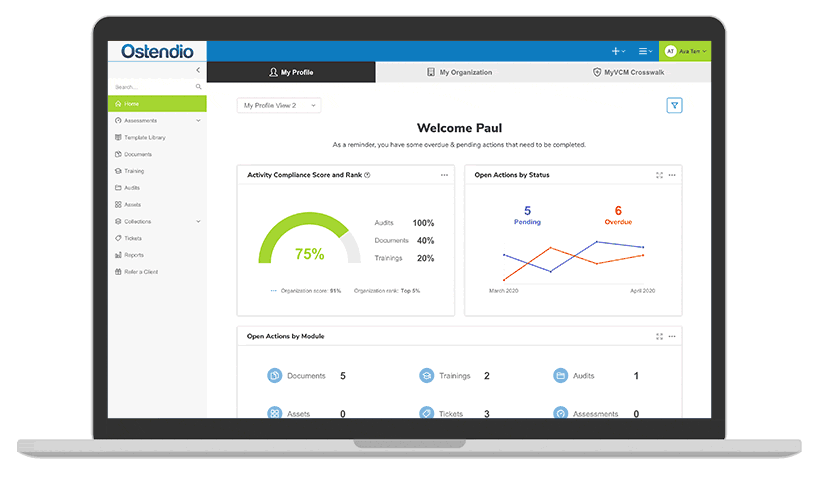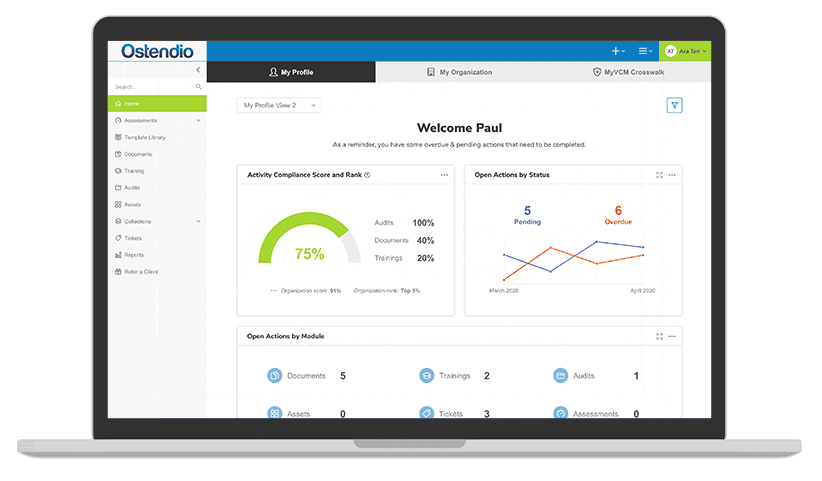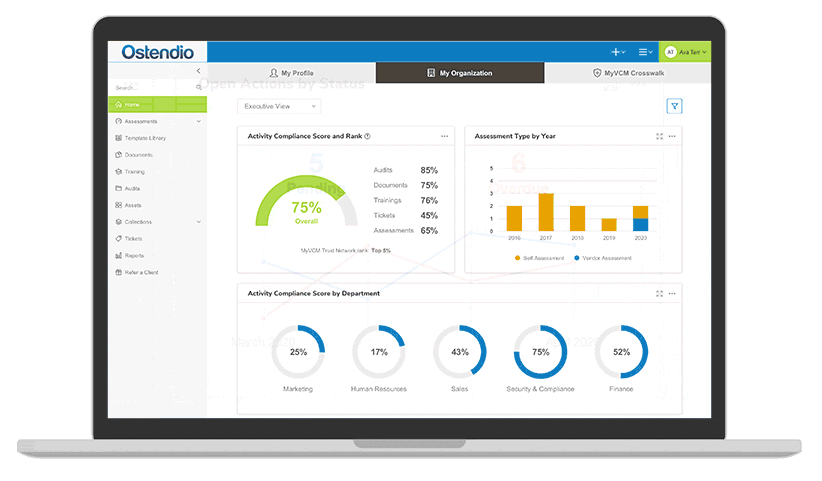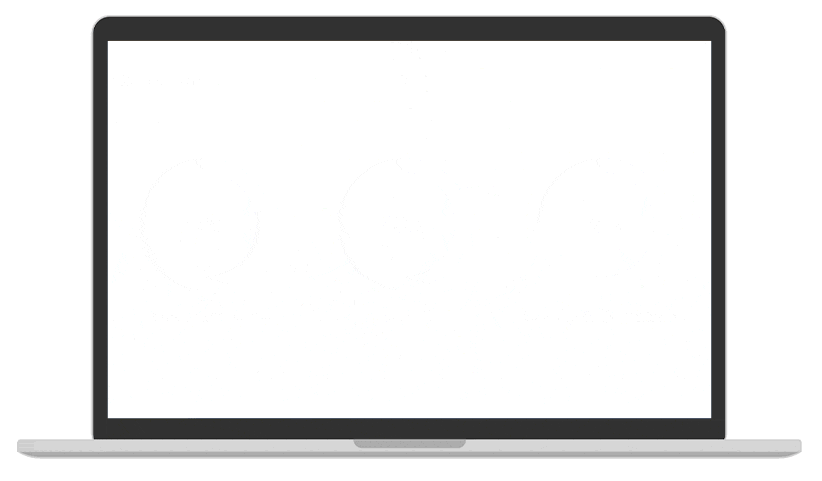 Image: The Ostendio MyVCM platform
Image: The Ostendio MyVCM platform
[Read more: The value of bringing in experts during a security audit]
Here are 5 ways you can take your cybersecurity program to the next level:
- 1. Expand your scope
One of the key elements of any security audit is defining the scope of the audit. Your initial security audit may have limited the scope to specific data sets, systems, departments, products or even people. Clearly one of the advantages of limiting scope is that it reduces the amount of work that has to be done to meet the security requirements. But often the focus on simplifying compliance can mean scope is narrowed at the expense of security. Also, a false sense of confidence can be gained if the organization erroneously thinks passing the audit applies more broadly. Review the scope of your initial audit, and look to see if there is an opportunity to expand it now you have successfully negotiated your first one.
- 2. Increase your maturity
Audits are rarely binary, where an organization needs to score 100% on all controls to pass. The Secure Control Framework CMM for example has a 6 stage maturity model, ranging from CMM 0 - Not Performed to CMM 5 - Continuously Improving. HITRUST also combines a maturity aspect based on documentation of policies where maturity levels range from non-compliant, somewhat compliant, and partially compliant to mostly compliant and fully compliant. So to ‘pass’ an audit it is typically only required to get above a certain threshold, which infers at least some level of failure and as such an opportunity for further improvement. These failures will usually be included within the audit report findings as areas that need to be addressed. Some of these may be critical, and must be addressed prior to receiving a pass certificate. Others may simply be noted in the final report, with the assumption the organization will commit to address them within a particular timeline.
- 3. Apply for multiple security standards
If you’ve already done the hard work of establishing your data security program now is the time to take it to the next level by applying for a security standard, or maybe multiple security standards. Establishing your security program is a great first step and this can be done with frameworks like NIST, PCI and ISO. However, being able to show that your security program meets more complex security standards like SOC 2, HITRUST and FedRAMP will require a security audit by an independent audit firm and will need to be updated on an annual basis to remain compliant. By using a platform that allows you to crosswalk evidence from one standard to another, your organization will save time when preparing for multiple security audits. The Ostendio MyVCM includes questionnaires to over 100 standards and regulations globally which makes this process more streamlined.
- 4. Include your vendors in your cybersecurity program
If you have established a data security program you know that your organization is documenting and protecting the sensitive information that it holds but what about your vendors? To take your cybersecurity program to the next level you should consider sending security assessments to your vendors, especially those who have access to your internal systems. A recent report showed that 53% of organizations have experienced one or more data breaches caused by a third party, costing them an average of $7.5 million to remediate. Remember that your data security is only as strong as your weakest link. To improve your security you need to make sure that all vendors maintain the same standards as you do.
- 5. Be ready to answer any security questions from your customers
Establishing a security program is a great step in protecting your business but it can also help you win business from your customers. We often hear from customers who have been surprised with the need to demonstrate compliance to security regulations in the late stages of contract negotiations. Don’t let that slow down your business. Take your security to the next level now and use a platform that helps you effectively showcase your security compliance.
Where do I start?
Improving your cybersecurity program includes investment in technology to help your business grow securely. However, this investment pales in comparison to the cost of a data breach and the damage that can be done to your company’s reputation following a breach. Many companies are caught off guard and data breaches in 2020 have already included brand names like MGM, Zoom and Twitter. Learning from these breaches and creating a culture of security in your organization reaching from the ground up will help protect your company.
A collaborative, integrated risk management platform, like Ostendio MyVCM, can help organizations of all sizes build, operate and showcase their security and risk management programs. Ostendio also helps companies improve their cybersecurity programs when they engage our Professional Services team. This group of industry experts is ready to help customers implement their security programs or supplement existing compliance teams when preparing for an audit.
By building on your established data security and risk management program you will be able to apply for multiple certifications, include vendors in your security program and showcase your program to customers. If you’d like to know more, speak to Ostendio and learn how the Ostendio MyVCM platform can help your business.

September 17, 2020

Comments